Use cases and security context
PLCnext Technology is supporting different security use cases:
- Openness is the leading approach, security is not a leading requirement:
- Industrial Security application note (AH EN INDUSTRIAL SECURITY) must be considered
- Security is an overall system design requirement, and is ensued by the system design:
- WBM offers support by User Management, Certificate Authority, Firewall, Syslog, etc.
- No security certification of the device is provided.
- A PLCnext Technology device is an IEC 62443-4-1/4-2 certified component:
- Security Profile must be activated.
- Security context described in this PLCnext Technology ‑ Security Info Center must fit the required automation system use cases.
- IEC 62443-3-3 and IEC 62443-2-4 system design and installation/maintenance processes are supported.
- Centralized security functions like Device and Update Management (DaUM), logging, backup and restore or OT PKI might be combined on an Edge Device and moved from the Service Management zone (IT) to the Manufactoring zone (OT) to separate IT and OT more strictly.
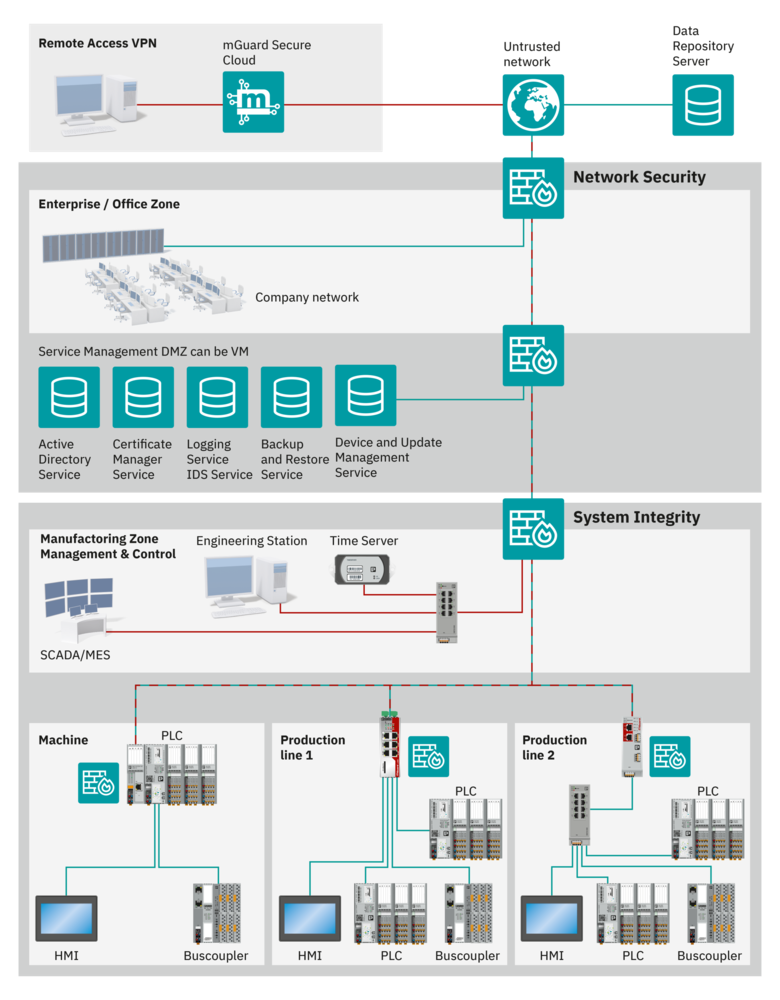
PLCnext Technology secure-by-design features
PLCnext Technology was developed according to the secure-by-design procedures from the beginning.
The next formal step was to certify the development process according to IEC 62443-4-1, and to prove the PLCnext Technology Security Level 2 feature set by an IEC 62443-4-2 certification.
To build an automation solution with PLCnext Technology based on the IEC 62443-4-1/4-2 certification the definitions described in this PLCnext Security Info Center must be fulfilled.
The activation of the Security Profile (Link) is mandatory.
The following features are building the base of the PLCnext Security.
Hardware measures
- TPM-protected Phoenix Contact device certificate
- Integrity check of devices while booting (depending in part on the controller model)
- Network segmentation by independent intefaces (e.g. the use of left-aligning AXC F XT ETH 1TX, depending on the controller model)
- Use of an SD card with encryption
Firmware measures
- Basing on Yocto Linux with secure-released components and automatic vulnerability supervision
- Secure communication via TLS 1.2, TLS 1.3, HTTPS, OPC UA®, SFTP, SSH, VPN
- User Manager supporting roles, permissions, credentials, and LDAP connection
- Certificate store for manufacturers, system integrators, and asset owners
- Firewall with management of different interfaces, levels for chains and rules
- Syslog-ng for secure message management and central storage
- Time synchronization via NTP
- Backup and restore via rsync
- Device and Update Management (DaUM) for e.g. firmware updates
• Published/reviewed: 2025-08-12 • Revision 019 •