Java RSC API ‒ Troubleshooting
Valid with firmware releases up to 2024.6
The Java RSC API has been replaced by a better solution, see Using gPRC communication.
Therefore the support for this tool is already discontinued. If you decide to use the Java RSC API anyway you'll be on your own. The Java RSC API for Windows or for Linux must already be installed on your computer; it can't be downloaded from the Phoenix Contact website any more.
In this topic, frequently occurring issues with the former Java RSC API are addressed.
Connection issues
If you run the application e.g. with the Java version 1.8.0_144 you might get the following exception:
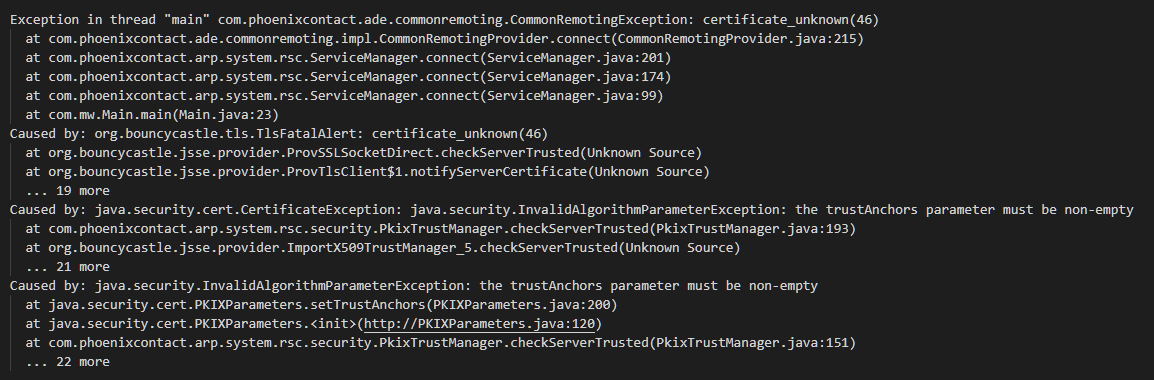
and the log message:
java.io.IOException: exception decrypting data - java.security.InvalidKeyException: Illegal key sizeThe reason for this issue is the limitation of AES to 128 bit key by the default JDK.
Execute the below steps to resolve the issue:
- Go to Oracle’s website and search for
Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files
. - Download the .zip file for your Java version and extract it on your drive.
- From the extracted folder, copy local_policy.jar and US_export_policy.jar files.
- Go to your_java_installation_directory/jre/lib/security and paste the copied files. These files will already be there, you just need to replace them.
- Run your application.
The problem should be solved.
Delays caused by random number generation
If you are running your application on the platform the SSLContext initialization with BouncyCastle could take quite a long time (up to 15 minutes) due to a low entropy platform. The library used for random number generation relies on /dev/random by default for UNIX platforms. This can block the process because on some operating systems /dev/random waits for a certain amount of “noise” to be generated before returning a result.
There are several solutions:
- Disable TLS verification.
- Use the SUN Provider if it is possible in your scenario.
- Although /dev/random is more secure, you could use /dev/urandom:
- Open $JAVA_HOME/lib/security/java.security (or for Java 9 $JAVA_HOME/conf/security/java.security) and change the line
securerandom.source=file:/dev/randomto
securerandom.source=file:/dev/urandom - It might also be required to change the line
securerandom.strongAlgorithms=NativePRNGBlocking:SUNtosecurerandom.strongAlgorithms=NativePRNGNonBlocking:SUN - Restart your application.
- Open $JAVA_HOME/lib/security/java.security (or for Java 9 $JAVA_HOME/conf/security/java.security) and change the line
Connection is closed after some time
The RSC connection will be closed after 5 minutes by default if there is no communication between client and device.
If you don’t want the connection to be closed you have to call a RSC service method regularly. Currently there is no keep alive mechanism.
 Security Note: Root privileges on the device are needed.
Security Note: Root privileges on the device are needed.We do not recommend and support this approach.
An other option is to disable the timeout. You must be the root user to edit the file. You have to set the sessionTimeout value to 0 and restart PLCnext.
The timeout is specified in the /etc/plcnext/device/System/RscGateway/RscGateway.settings file by the sessionTimeout attribute in the TcpGatewaySettings. The session timeout determines the time in milliseconds after a remote connection is discarded if no communication occurs.
...
<TcpGatewaySettings gatewayId="1" tcpPort="41100" sessionTimeout="300000" encrypted="true" identityStore="IDevID" />
...The first connection setup takes a lot of time
If you run the application on the device, the first connection attempt might take up to 35 seconds. The reason is the initialization time of the cipher suites and Bouncy Castle provider. You can call the com.phoenixcontact.arp.system.rsc.ServiceManager.initialize() method to do the initialization beforehand.
See also