User rights
Default user
PLCnext Controls are supplied with a preset admin user, and a default admin user password that is printed on the controller's housing.
Security note: Use the default
admin user password only for initial access and change it as soon as possible!
admin user
When a user logs onto a PLCnext Control with the admin user, the user is also recognized with the same name and password by the Linux® system. The user is therefore assigned to the plcnext group of the Linux® system. Files that this user may read, write to, and/or execute are assigned to the plcnext group file system.
plcnext_firmware user
The plcnext_firmware user is another major user in the Linux® system. It is permanently integrated, and it is used for starting the plcnext_firmware processes. In the Linux® system, this user can execute all required operations.
In addition to the Linux® user rights, the PLCnext Technology firmware also has its own user management, handled by means of the Web‑based Management. Its configuration is described in User Authentication (up to firmware release 2024.6) and in User management (from firmware release 2025.0).
Override with sudo
Executing Linux commands that require higher rights is made possible for the users via sudo. Which Linux commands the PLCnext users are allowed to execute via sudo is being configured in the Linux system.
POSIX™ ACLs
On secure-by-default devices with firmware 2025.0 or newer, also file and folder permissions/restrictions by means of access control lists (ACLs) can be present. For details see Access control lists.
Default rights settings
First generation of PLCnext Control devices
On AXC F x152, RFC 4072x, BPC 9x02S and EPC 15x2 devices the following rights are available:
| Rights | Restrictions | plcnext group |
admin | sudorequired |
Setting and inspecting IP settings (including ifconfig, ping, netstat, etc.) |
✓ | ✓ | ✓ ( ifconfig only) |
|
| Configuring the firewall | ✓ | ✓ | – | |
| Starting/stopping the firewall (see firmware scripts) | ✓ | ✓ | ✓ | |
Inspecting the firewall with nft |
✓ | ✓ | ✓ | |
| Configuring VPN (IPsec and OpenVPN™) | – | ✓ | – | |
| Starting/stopping VPN services (IPsec and OpenVPN™) | – | ✓ | ✓ | |
| Editing the Default PLCnext folder for individual ACF/ESM/GDS configurations and .so files | ✓ | ✓ | – | |
| Starting/stopping the PLCnext Technology firmware processes by shell scripts | – | ✓ | ✓ | |
Reading plcnext log files |
✓ | ✓ | – | |
Calling and configuring top and htop |
✓ | ✓ | – | |
Firmware update via update script with sudo update-plcnext |
only up to firmware 2024.6 | – | ✓ | ✓ |
| Configuring the NTP server | ✓ | ✓ | – | |
Setting the root password with passwd |
from firmware 2025.0 only with inactive Security Profile | – | ✓ | ✓ |
Requesting the system time with date |
✓ | ✓ | – | |
Setting the system time with sudo date -s |
✓ | ✓ | ✓ | |
Restarting/shutting down the controller with reboot or shutdown |
– | ✓ | ✓ | |
| Write access to /opt/plcnext and /opt/plcnext/projects | ✓ | ✓ | – | |
Recording network traces with tcpdump |
from firmware 2025.0 only with inactive Security Profile | ✓ | ✓ | ✓ |
Starting the gdbserver with root rights (see C++ remote debugging) |
– | ✓ | ✓ | |
Resetting to factory defaults with sudo recover-plcnext 1 (see Factory reset) |
only up to firmware 2024.6 | – | ✓ | ✓ |
Secure-by-default PLCnext Control devices
On secure-by-default devices (e.g. AXC F 1252) the following rights are available:
| Rights | plcnext group |
admin | sudorequired |
Setting and inspecting IP settings (including ifconfig, ping, netstat, etc.) |
✓ | ✓ | ✓ ( ifconfig only) |
| Configuring the firewall | ✓ | ✓ | – |
| Starting/stopping the firewall (see firmware scripts) | ✓ | ✓ | ✓ |
Inspecting the firewall with nft |
✓ | ✓ | ✓ |
| Configuring VPN (IPsec and OpenVPN™) | – | ✓ | – |
| Starting/stopping VPN services (IPsec and OpenVPN™) | – | ✓ | ✓ |
| Editing the Default PLCnext folder for individual ACF/ESM/GDS configurations and .so files | ✓ | ✓ | – |
| Starting/stopping the PLCnext Technology firmware processes by shell scripts | – | ✓ | ✓ |
Reading plcnext log files |
✓ | ✓ | – |
Calling and configuring top and htop |
✓ | ✓ | – |
Firmware update via update script with sudo update-plcnext |
impossible | impossible | impossible |
| Configuring the NTP server | ✓ | ✓ | – |
Setting the root password with passwd |
impossible | impossible | impossible |
Requesting the system time with date |
✓ | ✓ | – |
Setting the system time with sudo date -s |
✓ | ✓ | ✓ |
Restarting/shutting down the controller with reboot or shutdown |
– | ✓ | ✓ |
| Write access to /opt/plcnext and /opt/plcnext/projects | ✓ | ✓ | – |
Recording network traces with tcpdump |
✓ | ✓ | – |
Starting the gdbserver with root rights |
impossible | impossible | impossible |
Resetting to factory defaults with sudo recover-plcnext 1 (see Factory reset) |
– | ✓ | ✓ |
Root user
First-generation of PLCnext Control with inactive SecurityProfile only
For security reasons, accessing the controller as the root user is usually not recommended, and therefore prohibited with an active Security Profile. But for some commands, advanced user rights are required. To this end, the root user itself already exists under the Linux® system but the root user password needs to be set before accessing.
 Security Note: With
Security Note: With root user access, you can make unlimited changes on the controller. Root rights are therefore only suitable for qualified application programmers and software engineers with relevant experience.
- Avoid making changes to the PLCnext Technology firmware or to the operating system itself. If changes are inevitable, see Overlay File System for details.
- Do not supply the device with an already set password for the
rootuser. - Do not use the controller with an active
rootuser password for live operation; instead, return to an appropriate user role and remove therootuser password before live operation.
Setting a root user password
- Make sure the Security Profile is inactive.
- Connect to the controller via its IP address and log in as
adminuser. The default password for theadminuser is printed on the controller's housing. - Enter this command:
sudo passwd root - To authorize this command, enter the
adminuser's password . - Enter a new password for the
rootuser (minimum 5 characters, preferably consisting of upper-case and lower-case letters plus numbers). - Confirm the new password by entering it again.
Show the screenshotShow the screenshot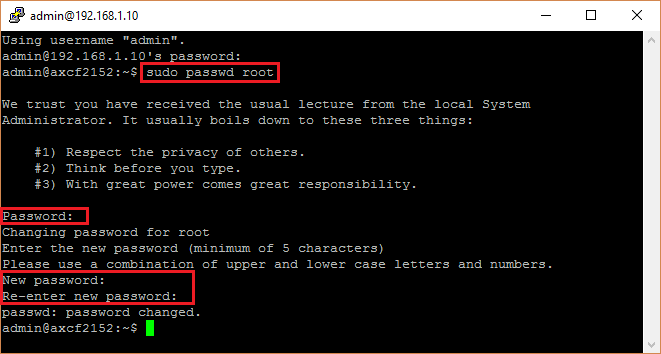
Using the root user
- Connect to the controller via its IP address and log in as
adminuser. The default password for theadminuser is printed on the controller's housing. - Switch to the
rootuser with thesu -command and therootuser's password. - Perform the activities that need the
rootuser's rights. - Once you have executed all the activities as the
rootuser, change back to the previous user role (e.g.,admin) using theexitcommand.
Removing the root password
If the root user is no longer required, remove the password. This prevents unauthorized users from modifying the firmware.
- Connect to the controller via its IP address and log in as
adminuser. The default password for theadminuser is printed on the controller's housing.
Security note: Use the default
adminuser password only for initial access and change it as soon as possible! - In the shell or command line interface, enter this command:
sudo passwd -dl root.
After that, the root user stays present on the controller. Before using it again you have to set a new password.
Recommended: The easiest way to undo changes to the root user is a reset type 1. This will also remove the root user's password.
SSH login as root user
First-generation of PLCnext Control with inactive SecurityProfile only
By default, the SSH login as a root user is prevented for security reasons. Nevertheless, they are some cases where the SSH login as the root user is necessary to perform commands that are reserved for the root user under a secure SSH connection.
To log in as a root user, the root user password must be set.
 Security Note: With
Security Note: With root user access, you can make unlimited changes on the controller. Root rights are therefore only suitable for qualified application programmers and software engineers with relevant experience.
- Avoid making changes to the PLCnext Technology firmware or to the operating system itself. If changes are inevitable, see Overlay File System for details.
- Do not supply the device with an already set password for the
rootuser. - Do not use the controller with an active
rootuser password for live operation; instead, return to an appropriate user role and remove therootuser password before live operation.
To enable or disable direct login via SSH for the root user, you have to configure this in the sshd_config file as shown here:
Activating SSH login as root user
- Connect to the controller and log in as the
rootuser. - Open the /etc/ssh/sshd_config file with a suitable editor.
- In the
# Authentication:section, enable thePermitRootLogin yesentry that is commented out by default. - Reboot the controller.
Deactivating SSH login as root user
- Connect to the controller and log in as the
rootuser. - Remove the file /etc/rfs/rw/upperdir/etc/ssh/sshd_config from the overlay file system on your controller.
- Reboot the controller.
Related Topics