Firewall configuration
Valid from firmware 2019.0 LTS up to 2024.6 - for firmware 2025.0 or newer see WBM 2: Security - Firewall
Accessibility
|
This WBM page is accessible with user role:
|
This WBM page is not accessible if this System Service has been disabled:
|
How to get into the WBMHow to get into the WBM
Establishing a connection to the Web-based Management (WBM):
- Open a web browser on your computer.
- In the address field, enter the URL https://<IP-address-of-the-controller>/wbm,
for example: https://192.168.1.10/wbm.
For further information, see WBM.
PLCnext Technology relies on the proven and commonly used Linux® firewall nftables. On the PLCnext Control, you don't need to configure the firewall rules via cryptic Linux shell commands: Just log on to the Web‑based Management and choose from the predefined basic rules, or add your own rules to the set.
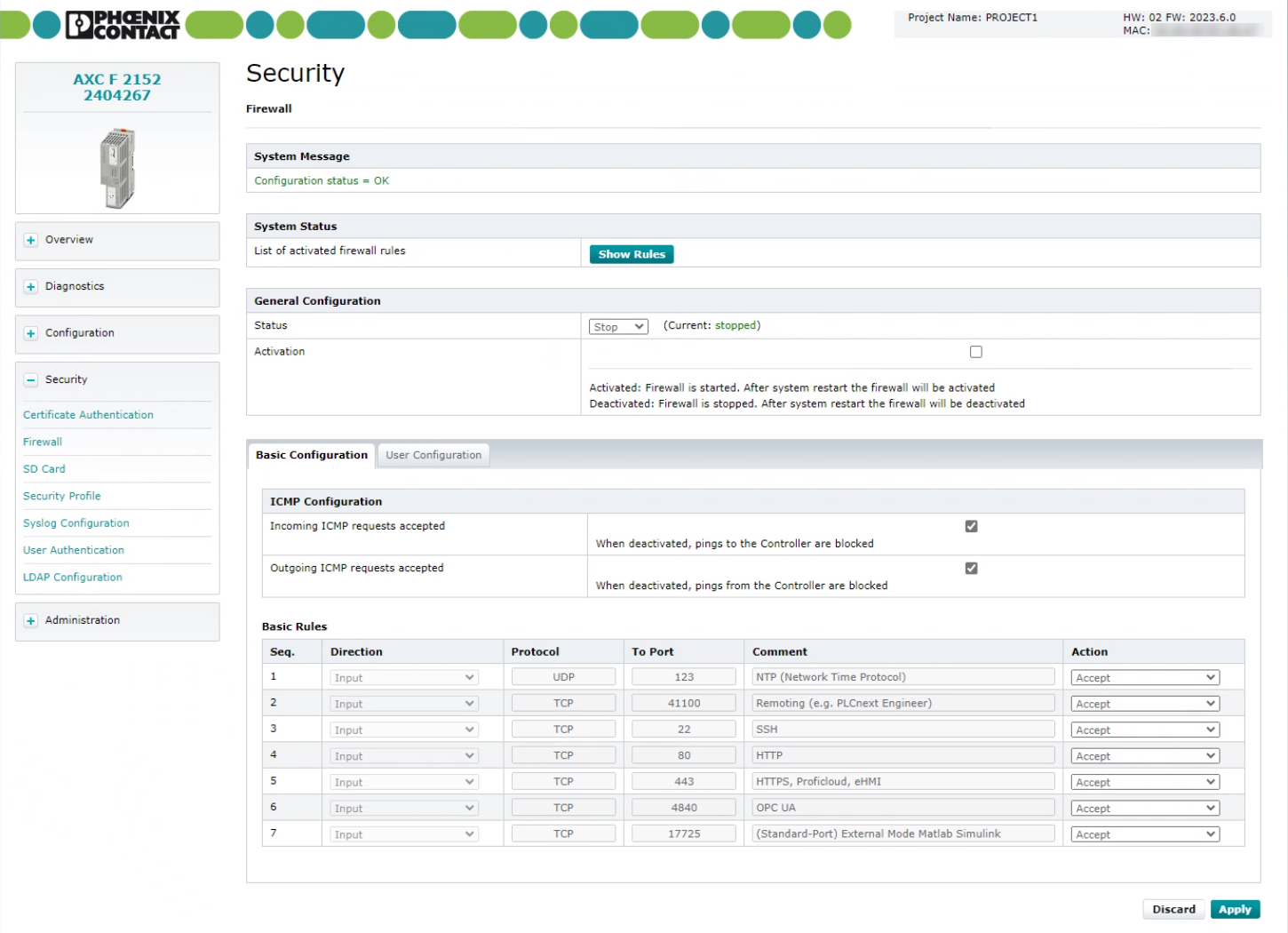
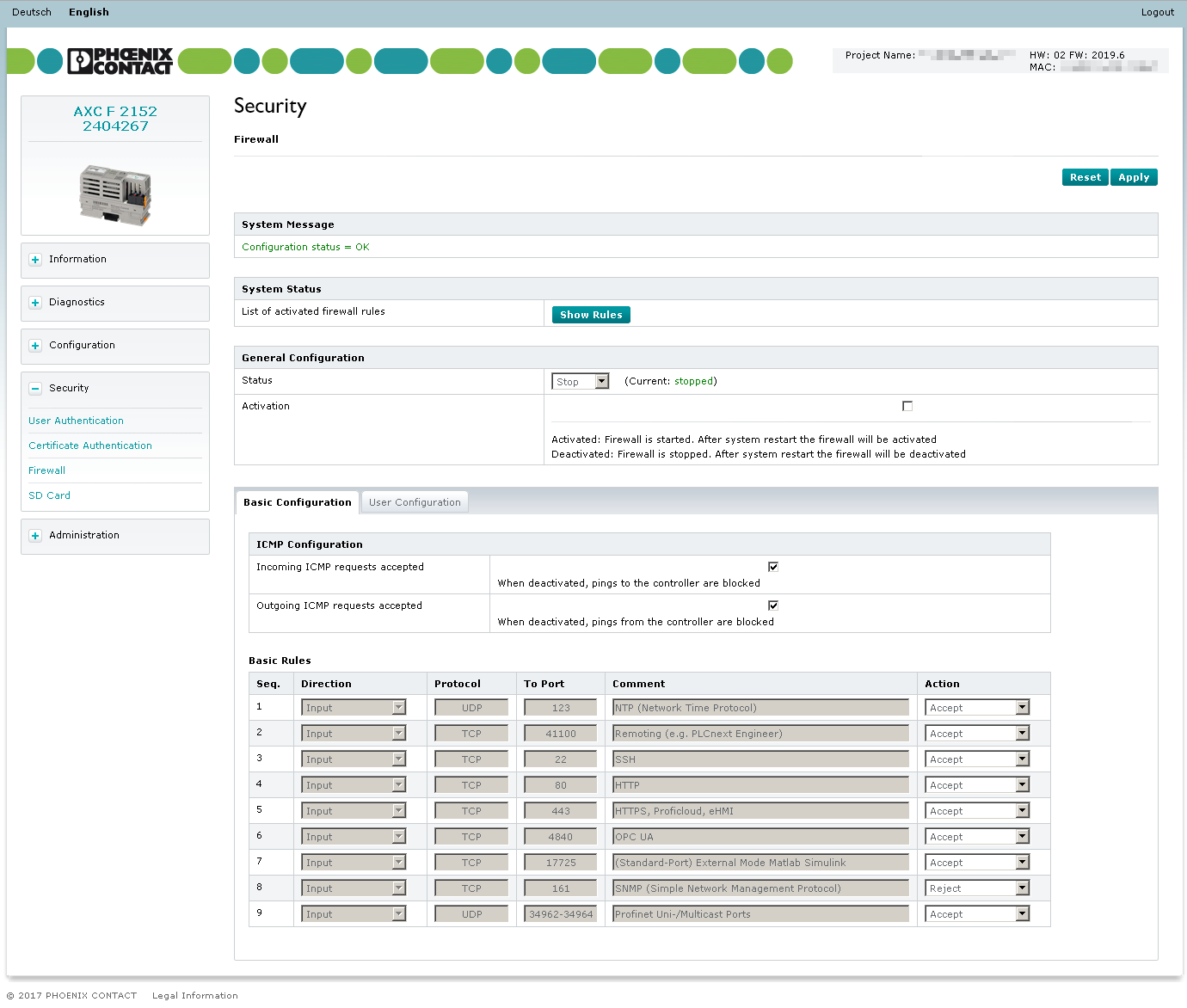
Show screenshot up to firmware version 2023.3Show screenshot up to firmware version 2023.3
Reset and Apply buttons
The buttons in the upper right corner of the page are used after changing settings in the sections below.
- To reset the firewall to default settings, click .
- To transfer changed firewall settings to the controller, click .
Known issue
Known for firmware 2024.0 LTS on all PLCnext Control devices:
If a firewall rule is defined by means of the WBM page and "Interface" as well as "Protocol" is set to "All" (and neither a specific port or IP address is set), then this rule is is not forwarded to the firewall. When picking a specific interface or protocol, the rule is applied correctly. (Note: Such rules have been set by customers to check the firewall or to exclude blocking by the firewall when debugging of network connections.) This issues is remedied in firmware 2025.0 already, and will be remedied for the preceding 2024.0 LTS with a hotfix soon.
System Message section
In the System Message section, responses and warnings regarding the transfer of settings to the controller are displayed. The following system messages can occur:
| System message | Description |
| Status=Ok | The configured firewall settings were successfully transferred to the controller. |
| Warning | A warning from the controller is issued, e.g., if one or several additional filter configurations are present in the system. The warning contains the designations of all additionally loaded filter tables. |
| Error | At least one firewall configuration is faulty. |
System Status section
If the firewall is active, you can generate an overview of all enabled firewall rules in a *.txt file.
- Click on in the System Status section.
↪ The *.txt file with the activated firewall rules is being generated and opens in a dialog box:
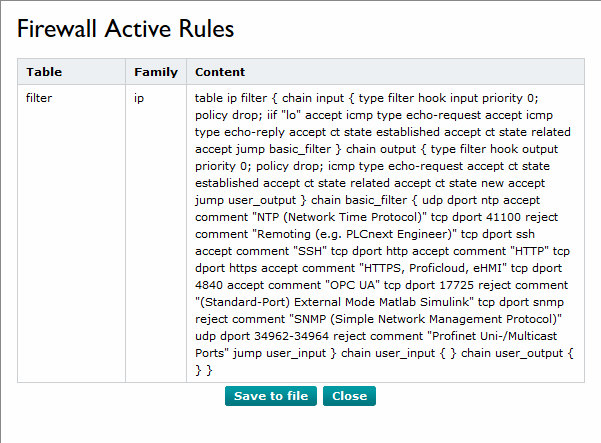
- To save the active rules to a *.txt file, click in the dialog box.
↪ The *.txt file is saved to a destination you can specify.
General Configuration section
In the General Configuration area, you can view the current firewall status (e.g., Current: stopped), temporarily activate or deactivate the firewall or permanently activate or deactivate the firewall.
Temporarily activating or deactivating the firewall
- To temporarily activate the firewall, select the Start or Restart entry from the drop-down list in the Status row.
To activate the configuration, click in the upper right corner.
↪ The firewall is activated. - To temporarily deactivate the firewall, select the Stop entry from the drop-down list in the Status row.
To activate the configuration, click in the upper right corner.
↪ The firewall is deactivated.
Note: After a restart of the controller this change will be reset.
Permanently activating or deactivating the firewall
- To permanently activate the firewall, enable the checkbox in the Activation row.
↪ The firewall is activated and remains activated even after a restart of the controller. - To permanently deactivate the firewall, disable the checkbox in the Activation row.
↪ The firewall is deactivated and remains deactivated even after a restart of the controller.
Configuring the firewall
Configuration of the firewall rules is divided into Basic Configuration and User Configuration.
The Basic Configuration tab provides predefined firewall rules while you can create your own firewall rules on the User Configuration tab.
Action column
The options for activating and deactivating the filter rules are available in the Action column on the Basic Configuration tab as well as on the User Configuration tab.
Select a setting from the drop-down list in the Action column for each firewall rule:
| Option | Description |
| Accept | Connections are accepted. The connection request is accepted. The connection can be established. |
| Drop | Connections are dropped. There is no response to the request. The packet is dropped. |
| Reject | Connections are rejected. The sender receives a response via the rejected connection. |
| Continue | The rule is not executed. Choose this option to skip the basic rule and instead use a user-specific rule for the port. User-specific rules are configured in the User Configuration area of the Web-based Management. |
To activate this configuration, click in the upper right corner.
Basic Configuration tab
On the Basic Configuration tab, the rules that are stored for the firewall upon delivery are displayed. For each rule, you can select how the respective connections are to be treated.
ICMP Configurations
In the ICMP Configurations section, you specify how incoming and outgoing ICMP echo requests are to be treated. Possible settings are:
- Incoming ICMP requests accepted
checkbox enabled: Incoming ICMP echo requests are accepted.
checkbox disabled: Incoming ICMP echo requests are blocked.
The controller cannot be reached using a ping command. - Outgoing ICMP requests accepted
checkbox enabled: Outgoing ICMP echo requests are accepted.
checkbox disabled: Outgoing ICMP echo requests are blocked.
Ping commands cannot be issued by the controller.
Basic Rules
The Basic Rules section provides predefined firewall rules for different incoming connections, which you can enable or disable in the Action column. The configuration baseline is stored in the /etc/nftables/plcnext-filter file in the controller file system.
The configuration baseline contains the following rules for incoming connections (Direction: Input).
- Select an action for each rule (see Action column):
| Description | Protocol | Port |
| NTP | UDP | Port 123 |
| Remoting (e.g. PLCnext Engineer) | TCP | Port 41100 |
| SSH connections, e.g., for SSH shell connection or SFTP connection | TCP | Port 22 |
| HTTP | TCP | Port 80 |
| HTTPS, (Proficloud,) eHMI and WBM | TCP | Port 443 |
| OPC UA® | TCP | Port 4840 |
| EtherNet/IP™ | TCP |
|
| MATLAB®/Simulink® in External mode | TCP | Port 17725 |
| PROFINET | UDP | Ports 49152 to 65535 (for better security, add the IP addresses of the PROFINET devices to the firewall input and output rules; see Activating PROFINET) |
| only part of the predefined Basic Rules up to 2023.3: PROFINET unicast/multicast ports |
UDP | Ports 34962 to 34964 |
| only part of the predefined Basic Rules up to 2023.3: SNMP |
UDP | Port 161 |
The settings are valid for all Ethernet interfaces. A limitation to certain Ethernet interfaces is specified via a user-specific rule in the User Configuration tab (see here).
With some activated firewall rules there is the risk that accessing the controller becomes difficult for you due to blocked ports. Restoring access permissions can result in the loss of user data.
Therefore, please consider the following notes when configuring basic rules:
Blocking the WBM access:
If you select the Reject or Drop action for basic rule no. 5 (TCP Port 443 - HTTPS, web server), you can no longer access the WBM of the controller after activating the rule by pressing . Therefore, you can then no longer change the firewall rules via the WBM.
- In case of a permanently started firewall (enabled Activation checkbox in the General Configuration section):
To stop the firewall in this case, you have to reset the controller to the default settings.
For more detailed information, please refer to the user manual for your controller.
Note that during a reset to the default settings, user-specific data (applications, configuration, etc.) is deleted.
Once the firewall is deactivated, you can again access the WBM. - In case of a permanently stopped firewall (disabled Activation checkbox in the General Configuration section):
The firewall is stopped after restarting the controller. You can again access the WBM.
Observe the following when using a PROFINET controller:
Up to firmware version 2023.3:
If you use the controller as PROFINET controller, you have to ensure that with an activated firewall, Accept is selected for basic rule no. 9 (UDP ports 34962-34964 - PROFINET unicast/multicast ports). Otherwise, establishing a connection to certain PROFINET devices is not possible.
From firmware version 2023.6:
The firewall rules no. 8 (SNMP) and no. 9 (PROFINET unicast/multicast ports) were removed from the default Basic Rules because PROFINET could almost not be used at all with an activated firewall using the default firewall rules of the PLCnext device. The rules could be misinterpreted that a PROFINET communication is possible even if the firewall is activated. At PLCnext Security Info Center - Activating PROFINET you can find instructions on how to configure the firewall to enable PROFINET communication.
Changing a basic rule
To change a basic rule, proceed as follows:
- In the Basic Configuration area, set the basic rule to Continue in the Action column. This way, this rule is skipped.
- Create a new rule in the User Configuration → Input Rules area.
- Configure the rule for the protocol and the port of the basis rule from the Basic Configuration area.
Example: You can specify incoming SSH connection requests via TCP port 22 in more detail by excluding certain IP addresses or exclusively establishing access of some IP addresses. - To make sure that all newly applied rules are actively used (even for already established connections!), restart the PLCnext Control device.
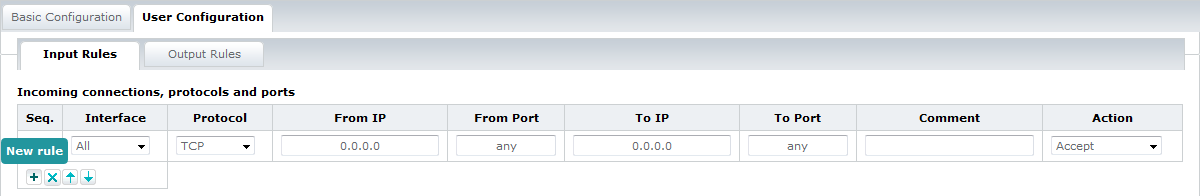
User Configuration tab
In addition or as an alternative to the basic rules, you can define and activate your own, user-specific firewall rules for different filter categories in the User Configuration tab. You can create new rules, delete rules or change the order of rules using the buttons at the end of the table.
Adding a new rule
To add a new Input rule, use the Input Rules tab on the User Configuration tab:
To add a new Output rule, use the Output Rules tab on the User Configuration tab:
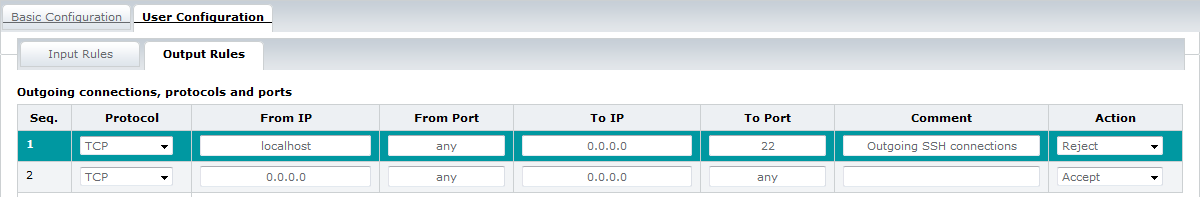
When working on a new rule, you will use these buttons:
| Button | Meaning | Function |
| New Rule | Adds a new filter rule | |
| Delete Rule | Deletes the selected filter rule | |
 |
Move rule up/down | Moves the filter rule upwards/downwards. The order determines the priority of the rules. |
You can define user-specific filter rules for specific ports, protocols and IP addresses for incoming (Input Rules tab) and outgoing (Output Rules tab) connections.
For a user-specific filter rule, define the following parameters:
| Column | Description |
| Interface ( Input Rules only) |
You can configure Input Rules specifically for an interface. From the drop-down list, select the desired Ethernet interface to which the filter rule is to be applied. The Output Rules apply to all interfaces. |
| Protocol | From the drop-down list, select the TCP, UDP, UDPLITE protocol or all of them. |
| From IP |
In the From IP field, enter an IP address, if applicable. |
| From Port | In the From Port field, enter the corresponding ports, if applicable. The rule applies to connections coming in from this address. You can specify all ports, single ports, or a value range. A port range is specified with a - without spaces between the port numbers. Example: 22-30 If you leave the field empty (any), all ports are selected. |
| To IP | In the To IP field, enter an IP address, if applicable. You can specify all IP addresses, a single IP address or a range. An IP address range is specified with a - without spaces between the IP addresses. Example: 192.168.1.10-192.168.1.20 If you leave the field empty (0.0.0.0), all IP addresses are selected. |
| To Port | In the To Port field, enter the corresponding ports, if applicable. The rule applies to connections going out to this address. You can specify all ports, single ports, or a value range. A port range is specified with a - without spaces between the port numbers. Example: 22-30 If you leave the field empty (any), all ports are selected. |
| Comment | Here, enter a description of the filter rule. |
| Action | The options described in Action column can be used as actions for the filter rules. |
To activate the settings you configured and transmit them to the system, click on the button. If a configuration is already present on the system, it is overwritten during this process.
To drop the current configuration and call the basic settings, click on the button.
To make sure that all newly applied rules are actively used (even for already established connections!), restart the PLCnext Control device.
Related Topics