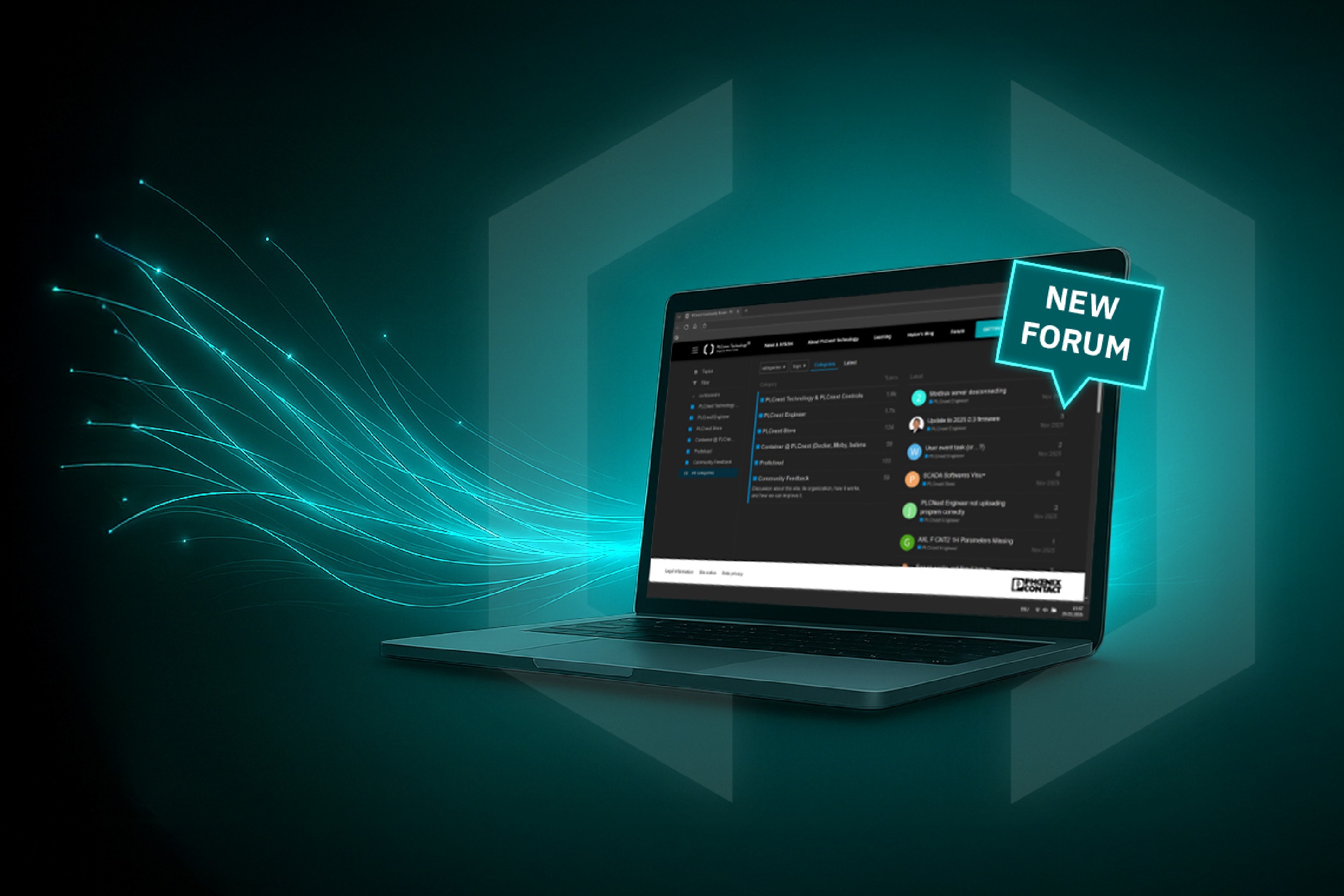
This is my archive
Security Profile: Configuring PLCnext Store Activating further system services can compromise security Before activating further system services, you must perform a risk and threat analysis of the system service and its impact on the security of the device and the application, taking into account the overall security context. Read More
Security Profile: Starting up The starting up of a PLCnext Control in a security context includes the following steps: Checking the device Deriving IP addresses Assigning IP addresses Activating the Security Profile Checking the integrity state Creating users Configuring TLS Generating self-signed HTTPS… Read More
Security Profile: Generic security concept Defense-in-depth design of automation systems is an important IEC 62443 process measure to achieve reliable security. The result is a generic layered architecture that leads step-by-step to a fully segmented network layer structure that describes the PLCnext Technology security architecture and the security use… Read More
Integrity check of downloaded software or firmware files IEC 62443 requires mandatory integrity check of software or firmware downloaded via Internet against tampering attacks. After downloading a setup file for any application (Windows®/Linux), a firmware file for a controller from the Internet or a PLCnext Technology App from the PLCnext Store,… Read More
Security Profile: Secure operation The secure operation of PLCnext Control in your specific application context requires a defined procedure. You will find all necessary steps in the following sections: Starting up: Everything you need to know when starting up your PLCnext Control in a security context. Environmental requirements: All environmental… Read More
Secure disposal You must safely decommission the controller so that no sensitive, confidential and/or manufacturer-specific data and software remain on the device. Check the national GDPR (General Data Protection Regulations) to comply with and make sure that attackers can’t access confidential security information’s from the deinstalled or disposed… Read More
Security Profile: Configuring the system time Centralized security logging only makes sense if all devices have a synchronized time. NTP is already supported today. TimeServer provides all devices with the same time base. For each device you have to configure which time server it should use. Use… Read More
Security Profile: Account management Operating a PLCnext Control in a security context includes the following steps regarding account management: Creating users Password complexity rules Checking the validity of passwords Configuring authentication errors and sessions Configuring Active Directory Connection • Published/reviewed: 2026-02-23 • Revision 021 • … Read More
Security Profile: Configuring central logging Logging in the security context only makes sense in a network. When configuring the SysLog, you set to which higher-level server the data is sent and which data it is. For information on basic security logging, refer to the topic Security logging. Read More
Security Profile: Configuring software updates Central software updates are possible via the Device and Update Management service. The Software Update via Device and Update Management service is activated by default. For further information on Device and Update Management, refer to the topic Device and Update Managementin the… Read More